Audit Specific User Permissions in SharePoint 2007 with PowerShell
In continuation with my earlier post: SharePoint Permission Report: Check Access Rights for a Specific User, got few requests to make the PowerShell script compatible with MOSS 2007. Hence, I’m posting the code here. Make sure you are running the script from Farm Admin credentials who has “FULL Control” Policy created on the Web Application!
It checks the following areas of SharePoint and generates a Log file as in the below screen:
- Farm Administrator’s Group
- Central Administration Web Application Policies
- Site Collection Administrators
- Scans the all Site collections and Sub-sites with Unique Permissions
- Scans all Lists and Libraries with unique permissions
- Scans all Groups which has permissions on sites and Lists
PowerShell Script to Check Access Rights for a Particular user all over SharePoint:
[System.Reflection.Assembly]::LoadWithPartialName("Microsoft.SharePoint")
#Get All Web Applications
Function global:Get-SPWebApplication($WebAppURL)
{
if($WebAppURL -eq $null) #Get All Web Applications
{
$Farm = [Microsoft.SharePoint.Administration.SPFarm]::Local
$websvcs = $farm.Services | where -FilterScript {$_.GetType() -eq [Microsoft.SharePoint.Administration.SPWebService]}
$WebApps = @()
foreach ($websvc in $websvcs) {
foreach ($WebApp in $websvc.WebApplications) {
$WebApps = $WebApps + $WebApp
}
}
return $WebApps
}
else #Get Web Application for given URL
{
return [Microsoft.SharePoint.Administration.SPWebApplication]::Lookup($WebAppURL)
}
}
Function global:Get-SPSite($url)
{
if($url -ne $null)
{
return New-Object Microsoft.SharePoint.SPSite($url)
}
}
Function global:Get-SPWeb($url)
{
$site= Get-SPSite($url)
if($site -ne $null)
{
$web=$site.OpenWeb();
}
return $web
}
Function GetUserAccessReport($WebAppURL, $SearchUser)
{
#Get All Site Collections of the WebApp
$SiteCollections = Get-SPWebApplication($WebAppURL)
$SiteCollections= $SiteCollections.Sites
#Write CSV- TAB Separated File) Header
"URL `t Site/List `t Title `t PermissionType `t Permissions" | out-file UserAccessReport.csv
#Check Whether the Search Users is a Farm Administrator
$ca= [Microsoft.SharePoint.Administration.SPAdministrationWebApplication]::Local.Sites[0].RootWeb
#Get Central Admin
$AdminSite = Get-SPWeb($ca.URL)
$AdminGroupName = $AdminSite.AssociatedOwnerGroup.Name
$FarmAdminGroup = $AdminSite.SiteGroups[$AdminGroupName]
foreach ($user in $FarmAdminGroup.users)
{
if($user.LoginName -eq $SearchUser)
{
"$($AdminSite.URL) `t Farm `t $($AdminSite.Title)`t Farm Administrator `t Farm Administrator" | Out-File UserAccessReport.csv -Append
}
}
#Check Web Application Policies
$WebApp= Get-SPWebApplication $WebAppURL
foreach ($Policy in $WebApp.Policies)
{
#Check if the search users is member of the group
if($Policy.UserName -eq $SearchUser)
{
#Write-Host $Policy.UserName
$PolicyRoles=@()
foreach($Role in $Policy.PolicyRoleBindings)
{
$PolicyRoles+= $Role.Name +";"
}
#Write-Host "Permissions: " $PolicyRoles
"$($WebAppURL) `t Web Application `t $($AdminSite.Title)`t Web Application Policy `t $($PolicyRoles)" | Out-File UserAccessReport.csv -Append
}
}
#Loop through all site collections
foreach($Site in $SiteCollections)
{
#Check Whether the Search User is a Site Collection Administrator
foreach($SiteCollAdmin in $Site.RootWeb.SiteAdministrators)
{
if($SiteCollAdmin.LoginName -eq $SearchUser)
{
"$($Site.RootWeb.Url) `t Site `t $($Site.RootWeb.Title)`t Site Collection Administrator `t Site Collection Administrator" | Out-File UserAccessReport.csv -Append
}
}
#Loop throuh all Sub Sites
foreach($Web in $Site.AllWebs)
{
if($Web.HasUniqueRoleAssignments -eq $True)
{
#Get all the users granted permissions to the list
foreach($WebRoleAssignment in $Web.RoleAssignments )
{
#Is it a User Account?
if($WebRoleAssignment.Member.userlogin)
{
#Is the current user is the user we search for?
if($WebRoleAssignment.Member.LoginName -eq $SearchUser)
{
#Write-Host $SearchUser has direct permissions to site $Web.Url
#Get the Permissions assigned to user
$WebUserPermissions=@()
foreach ($RoleDefinition in $WebRoleAssignment.RoleDefinitionBindings)
{
$WebUserPermissions += $RoleDefinition.Name +";"
}
#write-host "with these permissions: " $WebUserPermissions
#Send the Data to Log file
"$($Web.Url) `t Site `t $($Web.Title)`t Direct Permission `t $($WebUserPermissions)" | Out-File UserAccessReport.csv -Append
}
}
#Its a SharePoint Group, So search inside the group and check if the user is member of that group
else
{
foreach($user in $WebRoleAssignment.member.users)
{
#Check if the search users is member of the group
if($user.LoginName -eq $SearchUser)
{
#Write-Host "$SearchUser is Member of " $WebRoleAssignment.Member.Name "Group"
#Get the Group's Permissions on site
$WebGroupPermissions=@()
foreach ($RoleDefinition in $WebRoleAssignment.RoleDefinitionBindings)
{
$WebGroupPermissions += $RoleDefinition.Name +";"
}
#write-host "Group has these permissions: " $WebGroupPermissions
#Send the Data to Log file
"$($Web.Url) `t Site `t $($Web.Title)`t Member of $($WebRoleAssignment.Member.Name) Group `t $($WebGroupPermissions)" | Out-File UserAccessReport.csv -Append
}
}
}
}
}
#******** Check Lists with Unique Permissions ********/
foreach($List in $Web.lists)
{
if($List.HasUniqueRoleAssignments -eq $True -and ($List.Hidden -eq $false))
{
#Get all the users granted permissions to the list
foreach($ListRoleAssignment in $List.RoleAssignments )
{
#Is it a User Account?
if($ListRoleAssignment.Member.userlogin)
{
#Is the current user is the user we search for?
if($ListRoleAssignment.Member.LoginName -eq $SearchUser)
{
#Write-Host $SearchUser has direct permissions to List ($List.ParentWeb.Url)/($List.RootFolder.Url)
#Get the Permissions assigned to user
$ListUserPermissions=@()
foreach ($RoleDefinition in $ListRoleAssignment.RoleDefinitionBindings)
{
$ListUserPermissions += $RoleDefinition.Name +";"
}
#write-host "with these permissions: " $ListUserPermissions
#Send the Data to Log file
"$($List.ParentWeb.Url)/$($List.RootFolder.Url) `t List `t $($List.Title)`t Direct Permissions `t $($ListUserPermissions)" | Out-File UserAccessReport.csv -Append
}
}
#Its a SharePoint Group, So search inside the group and check if the user is member of that group
else
{
foreach($user in $ListRoleAssignment.member.users)
{
if($user.LoginName -eq $SearchUser)
{
#Write-Host "$SearchUser is Member of " $ListRoleAssignment.Member.Name "Group"
#Get the Group's Permissions on site
$ListGroupPermissions=@()
foreach ($RoleDefinition in $ListRoleAssignment.RoleDefinitionBindings)
{
$ListGroupPermissions += $RoleDefinition.Name +";"
}
#write-host "Group has these permissions: " $ListGroupPermissions
#Send the Data to Log file
"$($Web.Url) `t Site `t $($List.Title)`t Member of $($ListRoleAssignment.Member.Name) Group `t $($ListGroupPermissions)" | Out-File UserAccessReport.csv -Append
}
}
}
}
}
}
}
}
}
#Call the function to Check User Access
GetUserAccessReport "https://SharePoint.company.com" "Domain\User"
and the Output in Excel:
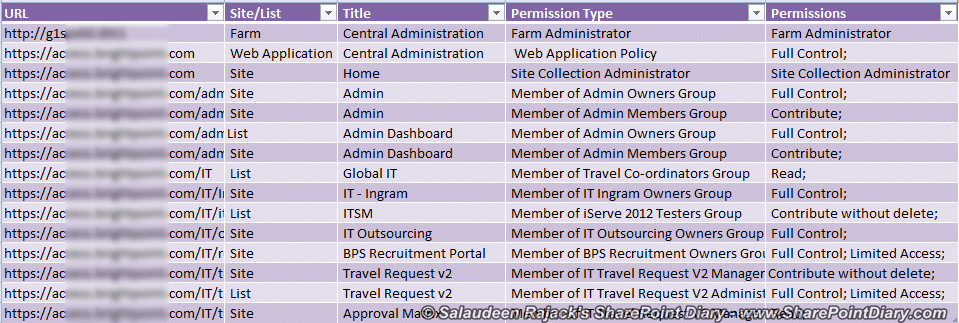

Hallo again,
First of all thank you for your efforts to make this work. I really appreciate it !
But is there a way to make this work, with Managed Paths ?
There must be a possibility to call a Webapp with MgdPath, and to look for every Sitecollection/Subsite/List under that managed path.
I am not a programmer, but I am trying to understand how it works…
Thank you !
This script scans all site collections with different managed paths of a web application!
Hallo,
This script is very handy, BUT where do I change the Web App URL ?! I cannot find the place…At the end of the script ?
Thank you for your efforts !
Hi There, Change it on Line#211
Hi I am no SharePoint admin and not keen on powershell.
I am using sharepoint 3.0. I ran this script and I get an excel file with only the headers and no other information?
URL ” ” Site/List ” ” Title ” ” PermissionType ” ” Permissions
What am I missing here? Is this script not compatible or is there a field I have to fill in on the script?
Thank you!
Make sure you are running this script from “Farm Administrator” login who has FULL control Web Application Policy granted. Change the Web App URL and User Accounts in the script accordingly.
Thanks so much 🙂
Hi,
I run the script and its generate a file with 1 kb size but give information about the personal site for the user.
Please let me know, where i am wrong.
Thanks and Regards,
Sabrina
The first parameter is: Web Application URL. Make sure you are providing it on your target SharePoint environment URL. Make sure you are running this script as “Farm Administrator” who has FULL control permissions.
Great PoweShell script, thanks for sharing it. This script is really very helpful for auditing a specific user permission in Sharepoint 2007. I tried an automate application named LepideAuditor for SharePoint tool (https://www.lepide.com/sharepoint-audit/) which helps to view who changed the permission for a specific user and get instant alerts on detecting changes to sites, lists, libraries, files/folders, servers, farms, content, groups, users, permissions etc.
Hi Salaudeeen,
This Script working for me, i got report successfully for specific group.
Now I need to Replace it with new group “xyz” with the same level of access.
Can you help on this
Thanks
i want to get all users with their access level, can you help plz
Here you go: https://www.sharepointdiary.com/2013/03/users-and-groups-report-based-on-permission-levels.html
thanks admin