SharePoint Online: Permission Report for Specific User in a Site Collection using PowerShell
Requirement: Generate a permission report to audit a specific user’s permissions in a given SharePoint Online site collection, sub-sites, all its lists, libraries, and list items.
How to Check User Permissions in SharePoint Online?
In SharePoint Online, managing user permissions is an important task to ensure secure access to sensitive information. Understanding the permissions assigned to a specific user can be helpful in managing the user’s access to a site collection. In this guide, we’ll explore how to generate a SharePoint Online permissions report for a specific user in a site collection using PowerShell. With this report, you can quickly and easily review the user’s permissions, identify any potential issues, and make informed decisions about granting or revoking access to sensitive information.
To get user permissions in SharePoint Online,
- Navigate to the SharePoint Online site on which you want to check permissions.
- Click on Settings Gear >> Site Settings >> Click on the “Site Permissions” link.
- On the Site permissions page, click the “Check Permissions” icon in the top ribbon under the Permissions tab.
- In the User/Group field, Enter the User Name you wish to verify permissions and click on the “Check Now” button.
- Shortly, You will see a list of permissions the user has on a site.
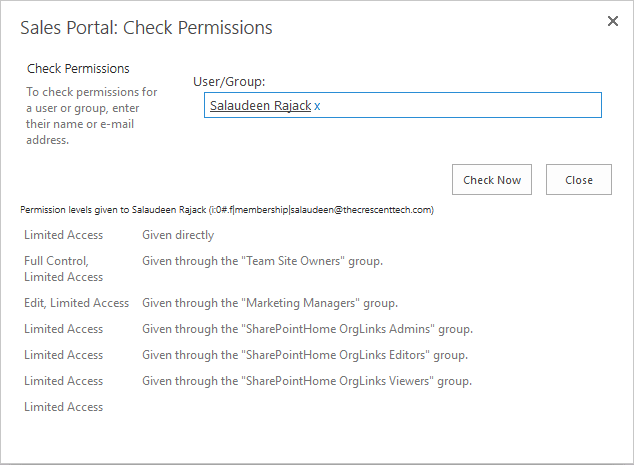
But the problem is: This method of checking user permissions shows access to one site at a time. You should repeat these steps on each site if you want to check user access for a site collection. So let’s use PowerShell to generate a user permissions report for SharePoint Online.
SharePoint Online PowerShell permissions report
Let’s use the PowerShell script to check user permissions in SharePoint Online. This PowerShell script checks user permissions and exports the findings into a CSV file. How to run this script? Change the Parameters from Line#6 to Line#8 according to your environment and hit run.
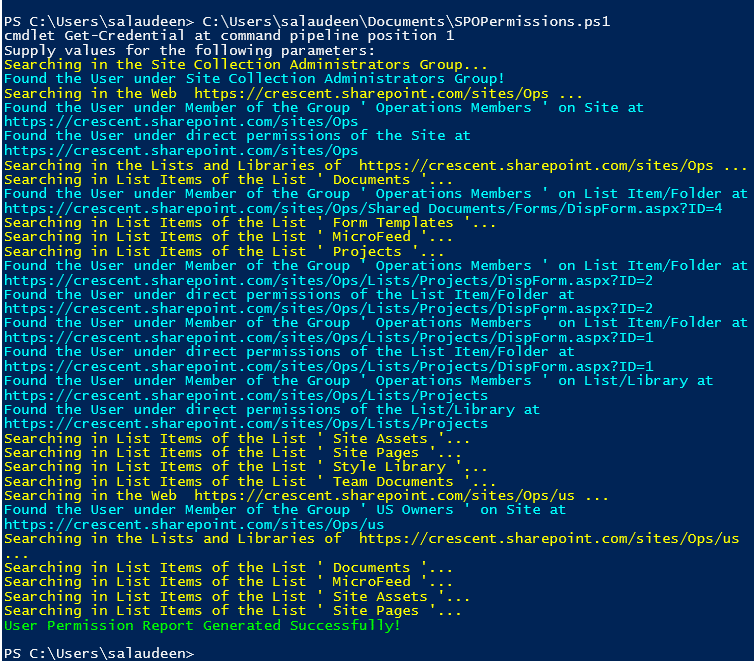
SharePoint Online: PowerShell to get user permissions on a given site collection
Here is how to check user permissions using PowerShell in SharePoint Online. Please note, there is a limitation in the script: This PowerShell script doesn’t scan Active Directory security groups!
#Load SharePoint CSOM Assemblies
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.dll"
Add-Type -Path "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.Runtime.dll"
#Set parameter values
$SiteURL="https://crescent.sharepoint.com/sites/ops"
$UserAccount="i:0#.f|membership|Salaudeen@crescent.com"
$ReportFile="C:\Temp\PermissionRpt.csv"
$BatchSize = 500
#sharepoint online powershell to get user permissions Applied on a particular Object, such as: Web, List, Folder or Item
Function Get-Permissions([Microsoft.SharePoint.Client.SecurableObject]$Object)
{
#Determine the type of the object
Switch($Object.TypedObject.ToString())
{
"Microsoft.SharePoint.Client.Web" { $ObjectType = "Site" ; $ObjectURL = $Object.URL }
"Microsoft.SharePoint.Client.ListItem"
{
$ObjectType = "List Item/Folder"
#Get the URL of the List Item
$Object.ParentList.Retrieve("DefaultDisplayFormUrl")
$Ctx.ExecuteQuery()
$DefaultDisplayFormUrl = $Object.ParentList.DefaultDisplayFormUrl
$ObjectURL = $("{0}{1}?ID={2}" -f $Ctx.Web.Url.Replace($Ctx.Web.ServerRelativeUrl,''), $DefaultDisplayFormUrl,$Object.ID)
}
Default
{
$ObjectType = "List/Library"
#Get the URL of the List or Library
$Ctx.Load($Object.RootFolder)
$Ctx.ExecuteQuery()
$ObjectURL = $("{0}{1}" -f $Ctx.Web.Url.Replace($Ctx.Web.ServerRelativeUrl,''), $Object.RootFolder.ServerRelativeUrl)
}
}
#Get permissions assigned to the object
$Ctx.Load($Object.RoleAssignments)
$Ctx.ExecuteQuery()
Foreach($RoleAssignment in $Object.RoleAssignments)
{
$Ctx.Load($RoleAssignment.Member)
$Ctx.executeQuery()
#Check direct permissions
if($RoleAssignment.Member.PrincipalType -eq "User")
{
#Is the current user is the user we search for?
if($RoleAssignment.Member.LoginName -eq $SearchUser.LoginName)
{
Write-Host -f Cyan "Found the User under direct permissions of the $($ObjectType) at $($ObjectURL)"
#Get the Permissions assigned to user
$UserPermissions=@()
$Ctx.Load($RoleAssignment.RoleDefinitionBindings)
$Ctx.ExecuteQuery()
foreach ($RoleDefinition in $RoleAssignment.RoleDefinitionBindings)
{
$UserPermissions += $RoleDefinition.Name +";"
}
#Send the Data to Report file
"$($ObjectURL) `t $($ObjectType) `t $($Object.Title)`t Direct Permission `t $($UserPermissions)" | Out-File $ReportFile -Append
}
}
Elseif($RoleAssignment.Member.PrincipalType -eq "SharePointGroup")
{
#Search inside SharePoint Groups and check if the user is member of that group
$Group= $Web.SiteGroups.GetByName($RoleAssignment.Member.LoginName)
$GroupUsers=$Group.Users
$Ctx.Load($GroupUsers)
$Ctx.ExecuteQuery()
#Check if user is member of the group
Foreach($User in $GroupUsers)
{
#Check if the search users is member of the group
if($user.LoginName -eq $SearchUser.LoginName)
{
Write-Host -f Cyan "Found the User under Member of the Group '$($RoleAssignment.Member.LoginName)' on $($ObjectType) at $($ObjectURL)"
#Get the Group's Permissions on site
$GroupPermissions=@()
$Ctx.Load($RoleAssignment.RoleDefinitionBindings)
$Ctx.ExecuteQuery()
Foreach ($RoleDefinition in $RoleAssignment.RoleDefinitionBindings)
{
$GroupPermissions += $RoleDefinition.Name +";"
}
#Send the Data to Report file
"$($ObjectURL) `t $($ObjectType) `t $($Object.Title)`t Member of '$($RoleAssignment.Member.LoginName)' Group `t $($GroupPermissions)" | Out-File $ReportFile -Append
}
}
}
}
}
Try {
#Get Credentials to connect
$Cred= Get-Credential
$Credentials = New-Object Microsoft.SharePoint.Client.SharePointOnlineCredentials($Cred.Username, $Cred.Password)
#Setup the context
$Ctx = New-Object Microsoft.SharePoint.Client.ClientContext($SiteURL)
$Ctx.Credentials = $Credentials
#Get the Web
$Web = $Ctx.Web
$Ctx.Load($Web)
$Ctx.ExecuteQuery()
#Get the User object
$SearchUser = $Web.EnsureUser($UserAccount)
$Ctx.Load($SearchUser)
$Ctx.ExecuteQuery()
#Write CSV- TAB Separated File) Header
"URL `t Object `t Title `t PermissionType `t Permissions" | out-file $ReportFile
Write-host -f Yellow "Searching in the Site Collection Administrators Group..."
#Check if Site Collection Admin
If($SearchUser.IsSiteAdmin -eq $True)
{
Write-host -f Cyan "Found the User under Site Collection Administrators Group!"
#Send the Data to report file
"$($Web.URL) `t Site Collection `t $($Web.Title)`t Site Collection Administrator `t Site Collection Administrator" | Out-File $ReportFile -Append
}
#Function to Check Permissions of All List Items of a given List
Function Check-SPOListItemsPermission([Microsoft.SharePoint.Client.List]$List)
{
Write-host -f Yellow "Searching in List Items of the List '$($List.Title)..."
$Query = New-Object Microsoft.SharePoint.Client.CamlQuery
$Query.ViewXml = "<View Scope='RecursiveAll'><Query><OrderBy><FieldRef Name='ID' Ascending='TRUE'/></OrderBy></Query><RowLimit Paged='TRUE'>$BatchSize</RowLimit></View>"
$Counter = 0
#Batch process list items - to mitigate list threshold issue on larger lists
Do {
#Get items from the list in Batch
$ListItems = $List.GetItems($Query)
$Ctx.Load($ListItems)
$Ctx.ExecuteQuery()
$Query.ListItemCollectionPosition = $ListItems.ListItemCollectionPosition
#Loop through each List item
ForEach($ListItem in $ListItems)
{
$ListItem.Retrieve("HasUniqueRoleAssignments")
$Ctx.ExecuteQuery()
if ($ListItem.HasUniqueRoleAssignments -eq $true)
{
#Call the function to generate Permission report
Get-Permissions -Object $ListItem
}
$Counter++
Write-Progress -PercentComplete ($Counter / ($List.ItemCount) * 100) -Activity "Processing Items $Counter of $($List.ItemCount)" -Status "Searching Unique Permissions in List Items of '$($List.Title)'"
}
} While ($Query.ListItemCollectionPosition -ne $null)
}
#Function to Check Permissions of all lists from the web
Function Check-SPOListPermission([Microsoft.SharePoint.Client.Web]$Web)
{
#Get All Lists from the web
$Lists = $Web.Lists
$Ctx.Load($Lists)
$Ctx.ExecuteQuery()
#Get all lists from the web
ForEach($List in $Lists)
{
#Exclude System Lists
If($List.Hidden -eq $False)
{
#Get List Items Permissions
Check-SPOListItemsPermission $List
#Get the Lists with Unique permission
$List.Retrieve("HasUniqueRoleAssignments")
$Ctx.ExecuteQuery()
If( $List.HasUniqueRoleAssignments -eq $True)
{
#Call the function to check permissions
Get-Permissions -Object $List
}
}
}
}
#Function to Check Webs's Permissions from given URL
Function Check-SPOWebPermission([Microsoft.SharePoint.Client.Web]$Web)
{
#Get all immediate subsites of the site
$Ctx.Load($web.Webs)
$Ctx.executeQuery()
#Call the function to Get Lists of the web
Write-host -f Yellow "Searching in the Web "$Web.URL"..."
#Check if the Web has unique permissions
$Web.Retrieve("HasUniqueRoleAssignments")
$Ctx.ExecuteQuery()
#Get the Web's Permissions
If($web.HasUniqueRoleAssignments -eq $true)
{
Get-Permissions -Object $Web
}
#Scan Lists with Unique Permissions
Write-host -f Yellow "Searching in the Lists and Libraries of "$Web.URL"..."
Check-SPOListPermission($Web)
#Iterate through each subsite in the current web
Foreach ($Subweb in $web.Webs)
{
#Call the function recursively
Check-SPOWebPermission($SubWeb)
}
}
#Call the function with RootWeb to get site collection permissions
Check-SPOWebPermission $Web
Write-host -f Green "User Permission Report Generated Successfully!"
}
Catch {
write-host -f Red "Error Generating User Permission Report!" $_.Exception.Message
}
And the result of the SharePoint Online user permissions reports using PowerShell: Script generates a CSV file in the below format.
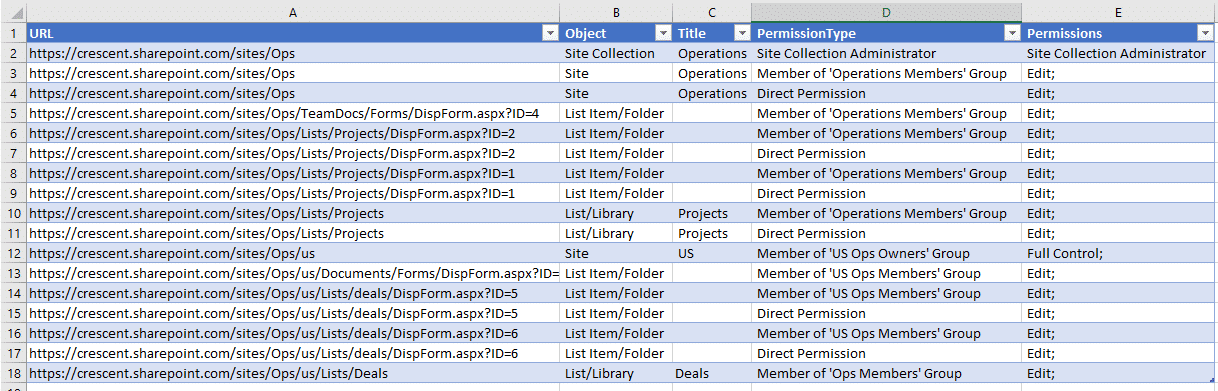
If you are looking for a permission report on all users of the site collection, use my other script: SharePoint Online: PowerShell Permissions Report
Wrapping up
In summary, generating a SharePoint Online permissions report for a specific user in a site collection using PowerShell is a useful tool for managing user access to sensitive information. This report provides a clear and concise overview of the user’s permissions, allowing you to quickly identify any potential issues and make informed decisions about granting or revoking access. Whether you’re a seasoned administrator or just getting started with SharePoint, this guide is an essential resource for managing user permissions in SharePoint Online. By using the script provided in this guide, you can generate a permission report and ensure secure access to sensitive information and maintain the integrity of your SharePoint environment.

Does someone have a done script: pemission report for all Sites for a specific user?
I do not have the knowledge to combine the function as you mentioned before Salaudeen.
Can I replace this instead
Original: #Set parameter values
$SiteURL=”https://crescent.sharepoint.com/sites/Ops”
$UserAccount=”i:0#.f|membership|Salaudeen@Crescent.com”
$ReportFile=”C:\Temp\PermissionRpt.csv”
to:
$SiteURL=”https://admin.crescent.sharepoint.com/”
$UserAccount=”i:0#.f|membership|Salaudeen@Crescent.com”
$ReportFile=”C:\Temp\PermissionRpt.csv”
so it will run on all site?
Combine Both the “Generate-PnPSitePermissionRpt” function and script under “How to Generate Report for All Site Collections in the Tenant?” to get permission report for all sites in the tenant.
Error Generating User Permission Report! Cannot process argument transformation on parameter ‘Web’. Cannot convert the “Microsoft.SharePoint.Client.Web” value of type “Microsoft.SharePoint.Client.Web” to type “Microsoft.SharePoint.Client.Web”.
Uh, what? it’s the same type already, this shouldn’t be a problem.
I did have to update the auth method because of MFA, it’s using
$AuthenticationManager = new-object OfficeDevPnP.Core.AuthenticationManager
$ctx = $AuthenticationManager.GetWebLoginClientContext($siteURL)
It gets the context just fine so I don’t know what the issue is about the object typing.
Salaudeen, this report is very valuable to many people. Great work!
I’m trying to do a similar query, but only want to return files from all sites that have a certain Sensitive Information Type (SIT) in them. For example, I have a Policy Rule in M365 Compliance that marks files as having SITs in them. I would like to know which of those files have been shared with more than say 500 users. If that’s not possible, it would be great to know which of those files with SITs are shared with “Everyone except external users”. Is this possible? Thanks in advance for any help on this!
Salaudeen,
I love this script and many of the other ones on your site. SharePoint Online: Permission Report for Specific User in a Site Collection using PowerShell has served me well but all of our accounts are now MFA. Do you have or plan to have an MFA version soon? Get-Credentials is just not working for me anymore. SharePoint Online: User Permissions Audit Report for a Site Collection using PnP PowerShell is my best alternative so far.
-Will
Id really appreciate this too. Or a explanation of how to update the existing script to allow for this.
Hi Salaudeen,
Thanks for your script. But i am getting the following error
Add-Type : Cannot bind parameter ‘Path’ to the target. Exception setting “Path”: “Cannot find path ‘C:\Program Files\Common Files\Microsoft Shared\Web Server
Extensions\16\ISAPI\Microsoft.SharePoint.Client.dll’ because it does not exist.”
At line:3 char:16
+ … -Type -Path “C:\Program Files\Common Files\Microsoft Shared\Web Serve …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : WriteError: (:) [Add-Type], ParameterBindingException
+ FullyQualifiedErrorId : ParameterBindingFailed,Microsoft.PowerShell.Commands.AddTypeCommand
Add-Type : Cannot bind parameter ‘Path’ to the target. Exception setting “Path”: “Cannot find path ‘C:\Program Files\Common Files\Microsoft Shared\Web Server
Extensions\16\ISAPI\Microsoft.SharePoint.Client.Runtime.dll’ because it does not exist.”
At line:4 char:16
+ … -Type -Path “C:\Program Files\Common Files\Microsoft Shared\Web Serve …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : WriteError: (:) [Add-Type], ParameterBindingException
+ FullyQualifiedErrorId : ParameterBindingFailed,Microsoft.PowerShell.Commands.AddTypeCommand
I cannot Web Server inside my Microsoft Shared folder.
Kindly advise. Thank alots
Please install either SharePoint Online PowerShell Module or Client-side object model Assemblies.
I totally forgot about sharing links. Which is a totally different way of sharing with everyone…….
It’s probably horrible, but for everyone on the root and everyone in a different group I did this (includes export). I do the same thing twice, once for root and once for groups on sites. The speed really depends on your tenant (the amount of sites and groups). I also don’t get the specific file or list which has permission, which would make the script way too complicated and unrunbale (we have 2500+ SharePoint sites)
here if you don’t have an app in your tenant>> https://docs.microsoft.com/en-us/sharepoint/dev/solution-guidance/security-apponly-azuread.
I have a different script for sharinglinks which basically does the same thing as the second part but only includes the sharinglink groups and gets me the sites who gave permission to sharinglinks groups….which are fortunately always named the same. We ended up not needing the sharinglinks groups.
Sidenote: if you want to disable sharinglinks only for the everyone group its not possible from the tenant….you have to also use a script for that.
here you go, don’t forget to change the property’s./
_____________________
#export location
$exportfile = “C:\AlleEveryoneRechten.csv”
#remove old export
Remove-Item $exportfile -Force
#make connection to be able to filter
$tenants = “your tenant ID”
$app = “your app id which has permission to do everything in sharepeoint”
$thumprint = “app thumprint”
Connect-PnPOnline -Tenant $tenants -ClientId $app -Thumbprint $thumprint -Url https://yourdomain.sharepoint.com
#my filter (I dont want all the sites)
$allesites=Get-PnPTenantSite|Where-Object{($_.url -ne “https://yourdomain-my.sharepoint.com/”) -and
($_.url -ne “https://yourdomain.sharepoint.com/portals/hub”) -and
($_.url -ne “https://yourdomain.sharepoint.com/sites/pwa”) -and
($_.url -ne “https://yourdomain.sharepoint.com/search”) -and
($_.url -ne “https://yourdomain.sharepoint.com/”) -and
($_.Template -ne “POINTPUBLISHINGPERSONAL#0”) -and
($_.template -ne “POINTPUBLISHINGTOPIC#0”) -and
($_.template -ne “REDIRECTSITE#0”)}|select Url
#per site connect
$allesites|foreach {
Connect-PnPOnline -Url $_.Url -Tenant $tenants -ClientId $app -Thumbprint $thumprint
#for getting everyone group on the root
$web = Get-PnPWeb -Includes RoleAssignments
foreach($ra in $web.RoleAssignments) {
$member = $ra.Member
$loginName = get-pnpproperty -ClientObject $member -Property LoginName
$loginNameAlleeneveryone = $loginName | where{ $_ -like “c:0-.f|rolemanager|spo-grid-all-users/$(Get-PnPTenantID)”}
$rolebindings = get-pnpproperty -ClientObject $ra -Property RoleDefinitionBindings
#if it finds something it will show it here
if ($loginNameAlleeneveryone -ne $null){
#make object and add to document ( ‘&’ will be edited to ‘en’)
$website=[scriptblock]::Create($web.Url)
#you can also use .RoleTypeKind instead of .Name
$rolebindingsrechten = [scriptblock]::Create(($rolebindings.Name -replace ‘&’,’en’))
#put data in file
[PSCustomObject]@{
Site = “$website”
Rechten = “$rolebindingsrechten (los op de site)”
Groep = “$null”} | Export-Csv $exportfile -Delimiter ‘;’ -notype -Append}
}
}
#per site connect
$allesites|foreach {
Connect-PnPOnline -Url $_.Url -Tenant $tenants -ClientId $app -Thumbprint $thumprint
#for everyone group in a group
$groups = Get-PnPGroup | Where {$_.IsHiddenInUI -eq $false -and $_.LoginName -notlike “SharingLinks*”}
foreach ($group in $groups){
$loginNameAlleeneveryoneINgroep = Get-PnPGroupMember -Group $group|where {$_.Title -eq “everyone except external users”}
$permissionVANgroup = Get-PnPGroupPermissions -Identity $group
#if it finds something it will show it here
if ($loginNameAlleeneveryoneINgroep -ne $null){
#make object and add to document ( ‘&’ will be edited to ‘en’)
$websitevoorgroup=[scriptblock]::Create($_.Url)
#you can also use .RoleTypeKind instead of .Name
$permissionVANgroupinfile = [scriptblock]::Create(($permissionVANgroup.Name -replace ‘&’,’en’))
$groupinfile = [scriptblock]::Create(($group.LoginName -replace ‘&’,’en’))
#put data in file
[PSCustomObject]@{
Site = “$websitevoorgroup”
Rechten = “$permissionVANgroupinfile”
Groep = “$groupinfile”} | Export-Csv $exportfile -Delimiter ‘;’ -notype -Append}
}
}
Thank you, above $UserAccount Parameter, $SiteURL is specified which will export data specific to the site. What would be the parameter if I have to replace it with the complete collection/tenant (e.g., https://example-admin.sharepoint.com )
You have to wrap everything inside a function and call the function by passing Site URL as the parameter. Here is an example: SharePoint Online: User Permissions Audit Report for a Site Collection using PnP PowerShell
Hi, Did you manage to get all sites with “everyone except external users”. I am having trouble running the script.
Use the $UserAccount Parameter with value: “c:0-.f|rolemanager|spo-grid-all-users/$(Get-PnPTenantID)” for “Everyone except external users”.
Thanks for your reply.
I cant do -Interactive because this is a scheduled task which must run on its own so I have to use -Tenant -ClientId -Thumbprint. This werked fine for other (less advanced) script. Is it also possible for this one? Can you tell me where I have to put this exactly? cause I got stuck on that.
I feel like it should be here:
#Get Credentials to connect
$Cred= Get-Credential
$Credentials = New-Object Microsoft.SharePoint.Client.SharePointOnlineCredentials($Cred.Username, $Cred.Password)
I changed it to:
#Get Credentials to connect
$Credentials = Connect-PnPOnline -Tenant $tenants -ClientId $app -Thumbprint $thumprint -Url https://mytenant.sharepoint.com
But unfortunately I get a forbidden or unauthorized depending on which $SiteURL I put in. (forbidden for https://mytenant.sharepoint.com/sites and unauthorized for https://mytenant.sharepoint.com).
I followed all the steps on https://www.sharepointdiary.com/2018/06/sharepoint-online-powershell-remote-server-returned-error-403-forbidden.html and I’m almost sure its because of step 6, my credentials type is not “SharePointOnlineCredentials”. Step 1 through 5 is fine. I tested it separately.
Is it possible to use object SharePointOnlineCredentials without username and password(legacy)?
I hope you can help me. Thanks in advance
Is there a way to get all sites where the ,Everyone expect external users, group has access to via modern authentication?
so with Connect-PnPOnline -Tenant $tenants -ClientId $app -Thumbprint $thumprint -Url $siteUrl
I can’t use cred. Legacy auth is turned off in our tenant
Connect-PnPOnline with -Interactive switch should work. For “Everyone Except External User”, use the LoginName as:
$LoginName = “c:0-.f|rolemanager|spo-grid-all-users/$(Get-PnPTenantID)”
Hi there,
Is there any chance to make it so the script skips over folders and items? With this in the script takes too long to run and usually crashes so if this could be removed that’d be great.
Cheers,
Jake
Use this script: SharePoint Online: User Permissions Audit Report for a Site Collection using PnP PowerShell
Receiving the message below on a large SharePoint site:
Error Generating User Permission Report! Exception calling “ExecuteQuery” with “0” argument(s): “The remote server returned an error: (429).”
Tried changing the batch to 100. Any other settings i can try?
Hello,
I receive the following error when attempting to run the script
Error Generating User Permission Report! Exception calling “ExecuteQuery” with “0” argument(s): “The remote server returned an error: (403) Forbidden.”
I am currently using SharePoint Online, and attempting to connect using the following:
$Cred= Connect-SPOService -Url https://birdconstruction-admin.sharepoint.com
Thank you,
You may be trying to access a site that you don’t have access to! Read more here: SharePoint Online: Fix “The remote server returned an error: (403) Forbidden” Error in PowerShell
HI there,
I am having issues running the report. I receive the following:
Error Generating User Permission Report! Exception calling :.ctor: with “2” arguments(s): “The ‘username’ argument cannot be null
Parameter name: username”
I’ve ensured I filled out the username field on line 7
What is causing the issue?
Thanks!
Would it be possible to modify the script to just ignore items and folders, just libraries and sites? the current script ran for about 30 minutes and then crashed on one of my site collections (too many objects I suspect)
Savin
Hi Savin, did you manage to figure this out? This is something I would like to try and implement also as with the items and folders it takes way to long to complete.
Cheers,
Jake
Please confirm the same script in pnp
Here you go: SharePoint Online: Permissions Report using PnP PowerShell
Thanks for the amazing script.
This script is breaking while enumerating External Lists….Any Suggestions?(PS: List is not deleted.)
Error Message:
Searching in List Items of the List ‘EAMS_Apps…
Error Generating User Permission Report! Exception calling “ExecuteQuery” with “0” argument(s): “Column ‘ID’ does not exist. It may have been deleted by another user. /sites/TS/Lists/EAMS_Apps”
Thanks for the amazing script.
This script is breaking while enumerating External Lists….Any Suggestions?(PS: List is not deleted.)
Error Message:
Searching in List Items of the List ‘EAMS_Apps…
Error Generating User Permission Report! Exception calling “ExecuteQuery” with “0” argument(s): “Column ‘ID’ does not exist. It may have been deleted by another user. /sites/TS/Lists/EAMS_Apps”
Hi Salaudeen,
If I need to get all the users within a specific library not just single user what parameter do I need to change?
Hi There, Use this Script: Get SharePoint Online Document Library Permissions Report using PnP PowerShell
We authenticate Via PKI, how would I Call a PKI authentication as a credential in the context?
I get the following error. I also have two factor enabled.
Connect-PnPOnline : The sign-in name or password does not match one in the Microsoft account system.
At line:11 char:1
Use: Connect-PnPOnline -Url $SiteURL -Interactive
I get the following error. I’m also using two factor. Maybe thats what is causing the problem?
Connect-PnPOnline : The sign-in name or password does not match one in the Microsoft account system.
At line:11 char:1
Refer here: Fix “The sign-in name or password does not match one in the Microsoft account system” Error in SharePoint Online
Hi.
Where can I get the 2 DLL files required for running this script? I can avoid using them if preloading SPOnline cmdlet first, but even though I’m feeling something is wrong because I don’t have those.
You need to install SharePoint Online PowerShell module! Install SharePoint Online PowerShell Module
Or download and install SharePoint Online Client SDK SharePoint Online Client SDK (Less recommended!)
Is there a way to remove limited access results from the output file?
Sure.. Set the $UserPermissions variable to ” ($RoleAssignment.RoleDefinitionBindings | Where { $_.Name -ne “Limited Access”}) -join “,”
I would replace the below with something better which will create different file names for each user.
Original
My code
Hi Salaudeen, I’m getting the error as mentioned above.. can you please let me know where to change the row limit?
In Line#158, set 500 to 100
Thanks for your reply. But it’s not working. I guess csom related scripts we can’t run in our environment. So do you have any other scripts which can pull the permission of a user in online sharepoint?
Can you elaborate the problem please? CSOM-PowerShell scripts can be run on any desktops with CSOM SDK installed.
Hi..
$RoleAssignment.Member.Users is available???. Seems to be not working..
Absolutamente bueno. Solo tengo un problema y es la conexion con el office 365
Reducing the Row Limit from 2000 to 500 resolves the problem: Exception calling “ExecuteQuery” with “0” argument(s): “The underlying connection was closed: An unexpected error occurred on a receive.”
Hi Salaudeen, I’m getting the below error
“Error Generating User Permission Report! Exception calling “ExecuteQuery” with “0” argument(s): “The underlying connection was closed:
An unexpected error occurred on a send.”
Please provide your comments and also how to change the row limit as mentioned above
In Line#9, set the $BatchSize to 100 from 500. Also, run the PowerShell console as “Administrator”.
Script working for small lists. Having problems with large lists. I am new to PowerShell. Can you please update the script to use linq to resolve performance issues?
Hi Salaudeen,
Thanks for your script.
As the result, it only shows the site permission information not including library and folder. Is it possible you can help to list the library permission with users and groups?
Appreciate it if you can help.
Use: SharePoint Online Site Permission Report using PowerShell
wonderfull.. you saved my day..
Adding one more If condition to full Security groups is working absolutely fine.
$RoleAssignment.Member.PrincipalType -eq “SecurityGroup”
awesome script !!! thank you.